Welcome to Commerce.com's Trust Center.
At Commerce.com, security, privacy, resilience, and responsible AI development are foundational to our platform. We are committed to delivering a secure, reliable, and trustworthy e-commerce experience for you and your customers.
What Sets Us Apart
Best-in-Class Payment Security
BigCommerce maintains Level 1 PCI DSS Attestations of Compliance as both a Merchant and a Service Provider—the highest level available. This simplifies your compliance and demonstrates our commitment to protecting payment data.
Proactive Threat Defense
We partner with Recorded Future and collaborate with security communities like RH-ISAC, InfraGard, and CISA to monitor and respond to evolving threats before they impact your business.
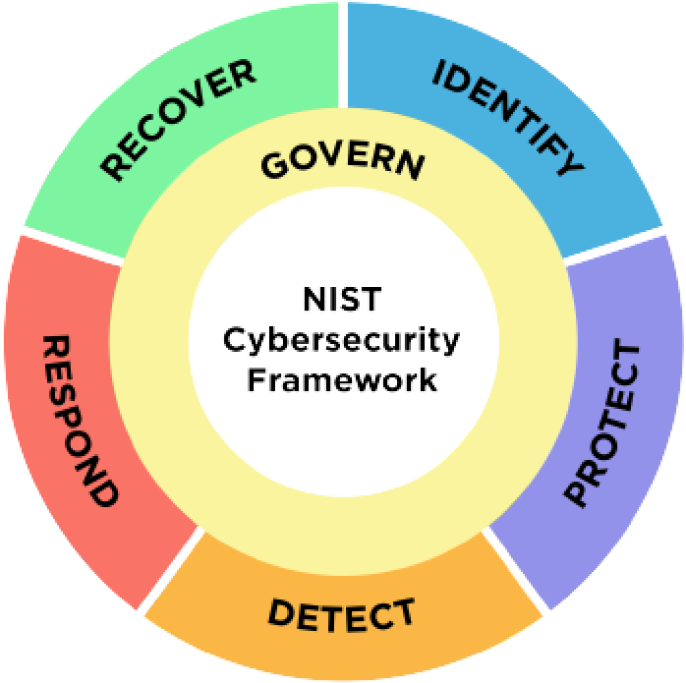
Proven Compliance Frameworks
Our security program is aligned with the NIST Cybersecurity Framework and certified against globally recognized standards, including ISO/IEC 27001:2022, 27017, 27018, 27701, and 22301, ensuring rigorous risk and continuity management.
Purpose-Built for Enterprise E-commerce
Unlike general-purpose platforms that can hold you back, BigCommerce empowers you with the scalability, control, and advanced security features needed to thrive in the complex world of enterprise e-commerce.
Responsible AI, Certified Under ISO/IEC 42001
BigCommerce is among the first to certify against ISO/IEC 42001:2023, the international AI management system standard. Our use of AI—for fraud prevention, recommendations, and personalization—is governed by principles of transparency, safety, and accountability.
Built for Enterprise E-commerce
We’re purpose-built for the complexity of enterprise retail, providing the scale, control, and advanced security features global businesses demand.
Security You Can Manage
We provide the tools to help you manage your store’s privacy and security. You stay in control—while we ensure the platform beneath you stays trusted.
Stay Informed
Subscribe to this Trust Center for the latest security updates and compliance resources.
Contact Us
Privacy: privacy@bigcommerce.com
Security: security@bigcommerce.com
Sales & Support: https://www.bigcommerce.com/contact


























Documents
- Are the policies and procedures reviewed and updated at least annually?
- Are background verification policies and procedures designed according to local laws, regulations, ethics, and contractual constraints and proportional to the data classification to be accessed, business requirements, and acceptable risk?
- Is a risk-based corrective action plan to remediate audit findings established, documented, approved, communicated, applied, evaluated, and maintained?
- Are cryptographic keys revoked and removed before the end of the established cryptoperiod (when a key is compromised, or an entity is no longer part of the organization) per defined, implemented, and evaluated processes, procedures, and technical measures to include legal and regulatory requirement provisions?
- Are processes, procedures, and technical measures to manage archived keys in a secure repository (requiring least privilege access) being defined, implemented, and evaluated to include legal and regulatory requirement provisions?
Security Advisory: React Server Components CVE-2026-23864
We are aware of the recently disclosed React Server Components vulnerability, CVE-2026-23864 (CVSS 7.5), which affects certain versions of React Server Components used by frameworks such as Next.js.
Commerce.com is not affected by this vulnerability.
We have not identified any impact to our platform or customer environments.
The vulnerability relates to denial-of-service scenarios triggered by specially crafted HTTP requests to React Server Component server functions. Importantly, this issue does not allow for remote code execution.
We recommend that customers who independently use React Server Components in their own applications review the advisory and upgrade to a patched version if applicable.
More information:
https://vercel.com/changelog/summary-of-cve-2026-23864
Patched versions are available for affected React and framework releases, and users should upgrade as recommended by their framework maintainers.
A critical severity vulnerability related to React Server Components has been disclosed affecting React versions 19.0, 19.1, and 19.2.
A critical severity vulnerability related to React Server Components has been disclosed affecting React versions 19.0, 19.1, and 19.2. This includes Next.js which is used for internal applications at Commerce as well as customers building storefronts using Catalyst and Makeswift. For further details on the vulnerability, refer to Critical Security Vulnerability in React Server Components. https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
To avoid exposure, Next.js and React need to be updated to their latest patched versions.
If you’re hosting your application on Vercel or are using Cloudflare’s WAF, those providers have platform level protections that help mitigate this vulnerability. However, upgrading to the latest versions of Next.js and React is strongly recommended. For further details refer to the Vercel (https://vercel.com/changelog/cve-2025-55182) and Cloudflare (https://blog.cloudflare.com/waf-rules-react-vulnerability/) blog posts.
Here’s what else you need to know specific to Commerce.
Actions we are taking
All affected Next.js applications at Commerce have been upgraded to a patched version of Next.js, addressing the vulnerability. We’ve also released Catalyst v1.3.5 which ships with a patched version of Next.js.
Actions you need to take
If you are running a Catalyst-based headless storefront, you will need to update it to a version that includes the patched releases of Next.js and React. The following Catalyst versions incorporate these fixes.
@bigcommerce/catalyst-core@1.3.5
@bigcommerce/catalyst-makeswift@1.3.6
For migration details, refer to the Catalyst 1.3.5 Release Notes.
If you’re using a version of @bigcommerce/catalyst-b2b-buyer-portal, follow the manual steps outlined in the release notes. https://developer.bigcommerce.com/docs/storefront/catalyst/release-notes/1-3-5
Makeswift
Makeswift customers that are not using Catalyst should follow the Makeswift blog post for specific mitigation steps. https://www.makeswift.com/blog/announcements/2025-12-03-react-server-components-vulnerability
2025 Penetration and Network Segmentation Test Summaries Posted
As part of Commerce.com's continued commitment to transparency and best-in-class security practices, we have completed our 2025 third-party penetration and network segmentation assessments. Executive summaries of these evaluations are now available in the REPORTS section of our Trust Center.
These annual tests assess the security posture of our applications, APIs, and mobile apps, feed management system, and include a comprehensive suite of network assessments—covering both internal and external networks, production segmentation, and the logical separation between customer storefronts.
Together, these assessments validate the effectiveness of our overall security architecture and ensure the confidentiality, integrity, and availability of the Commerce.com platforms.
All findings were reviewed and addressed in accordance with our risk management framework and remediation SLAs: 10 days for critical, 30 days for high, and 90 days for medium severity issues.
To view the executive summaries, visit security.bigcommerce.com and navigate to the REPORTS card.
European Accessibility Act (EAA)
We're committed to creating an inclusive experience for all our customers. As part of this commitment, we want to inform you about the European Accessibility Act (EAA), which came into effect on June 28, 2025. This significant legislation aims to make a wide range of products and services, including digital platforms, more accessible for people with disabilities across the EU. We are actively working to ensure our offerings comply with these new standards, reflecting our dedication to universal access and an enhanced user experience for everyone.
Annual Audit Complete: 2025 Certifications and Reports Available
Script Authorization on Payment Pages: Understanding PCI 4.0 Section 6.4.3 and How We’re Providing The Tools To Keep Your Payment Pages Secure: https://developer.bigcommerce.com/resource-hub/script-authorization-on-payment-pages
We're pleased to announce the successful completion of our 2025 annual audit!
As part of our commitment to transparency and security, our updated ISO certifications, SOC Reports, and PCI Attestations are now available for your review. You can access all of these documents directly from our Platform Trust Center: https://bigcommerce.com/security
Thank you for your continued trust and partnership.
